How I hacked my luxury local sports studio (and two others)
One day I decided to take a look at the application that my sports club uses. They use a software for studio management, covering everything from bookings and payroll to marketing and more. I began looking at the application because my sports club website was already a bit wonky and I was pretty sure something could be hacked. I was right.
For a little context, I work as a penetration tester in cybersecurity, so I knew what and where to look.
I found two access control vulnerabilities in the software that is used by multiple sport studios.
The SaaS behind the API
Their versatility and ease-of-use makes them popular amongst sport studios, which is why these vulnerabilities applied to most, if not all, of the studios that use their software. In my city (Brussels), I have noticed at least 3 sport studios that use their software and thus had the identified vulnerabilities present in their application.
Two vulnerabilities for free exercise
In this section I cover how I found a way to steal credits or even “buy” a pass for free sport classes.
1. Stealing class credits
When a user creates an account, they receive what is called a consumer_payment_pack or also just a payment_pack ID. If you haven’t purchased any subscriptions or passes, it is basically valued to zero. Once you purchase a subscription or pass, you will receive a new ID. The issue here is that class passes are not account-bound, and there is no server-side validation. This means that, if someone knew the ID, it would be possible for them to book a class using another user’s payment_pack ID. This is a problem for two reasons:
- You can brute force a random payment pack ID. The pattern can be recognizable, and then brute force only 4 numbers, 10.000 possibilities (keep in mind that, depending on the server, this could take only a few minutes).
- You could also create temporary accounts to buy the discounted trial pass and use that account’s payment pack ID.
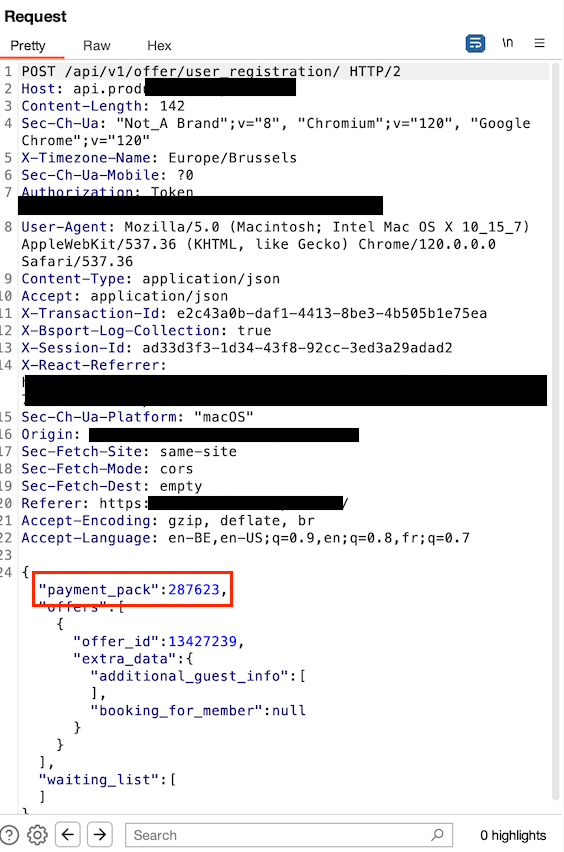
Image 1 is a screenshot of a class booking request I intercepted using Portswigger’s tool Burp Suite. If I were to send the request as it were, I would indeed get a [200 OK] response, but the front-end would redirect me to the subscriptions/pass store, where I would need to purchase class credits in order to validate my booking.
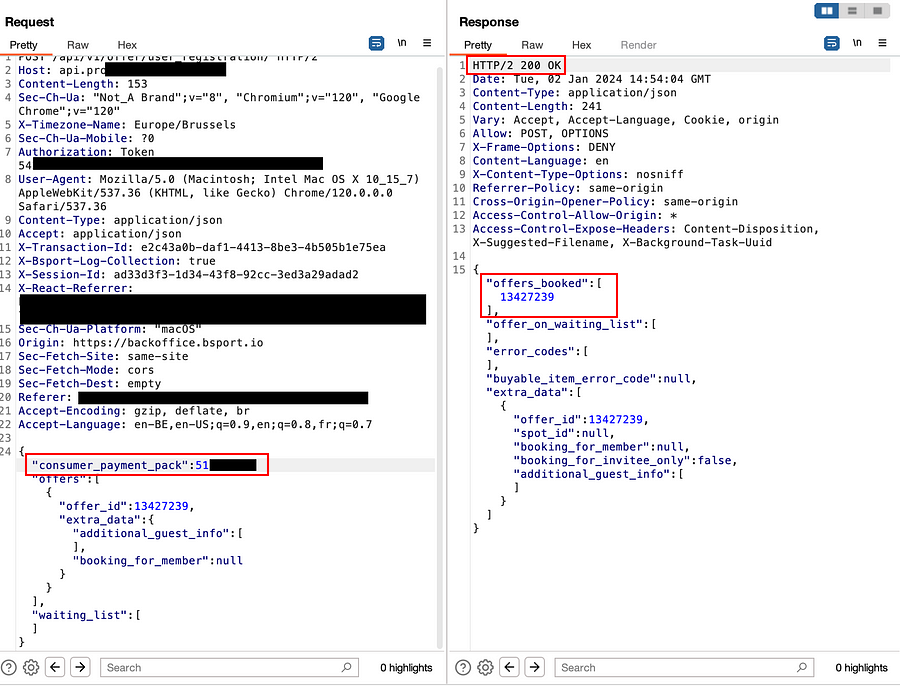
As you can see on image 2, I was able to book a class using the payment pack ID of another account. The validation is shown by the “offers_booked” parameter in the response body. Disclaimer: for testing purposes, I had created a separate account.
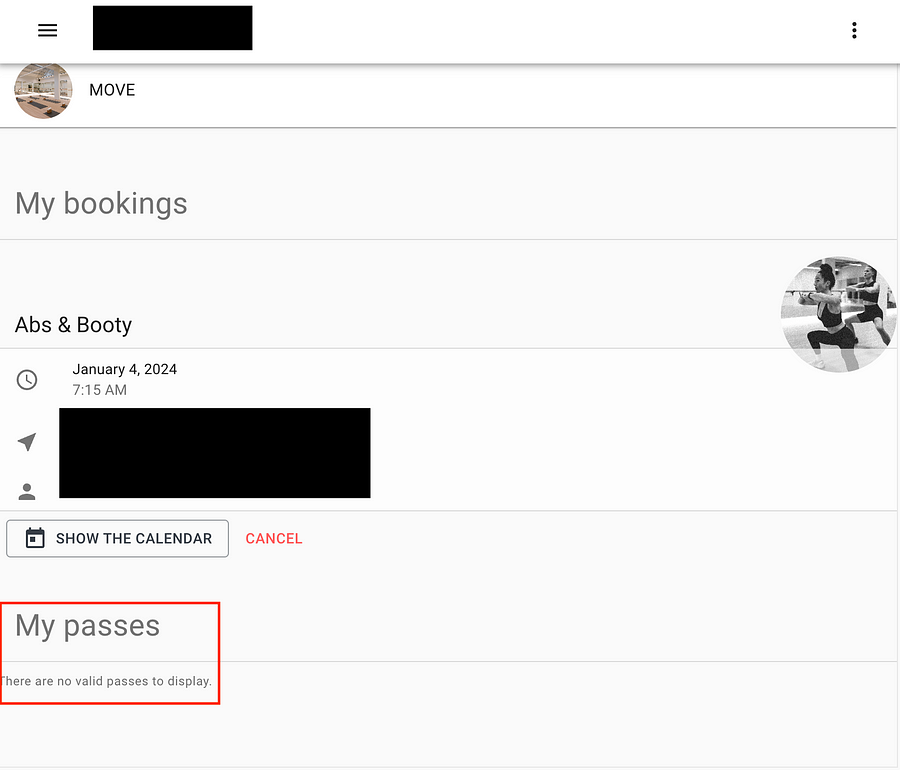
On image 3, I am highlighting the fact that I do not have any subscriptions or passes available on my account, yet I was still able to book a sports class by using the payment pack ID of another account.
2. Secret manager’s page
It was possible to access a managers-only page and get a free subscription pass although the page is normally not supposed to be accessible to regular users.
If a regular user wants to buy a subscription, they are redirected to the subscription page, as seen below:

But if you know the magic word (=true), you can access a secret page called the manager’s page, where everything is free.
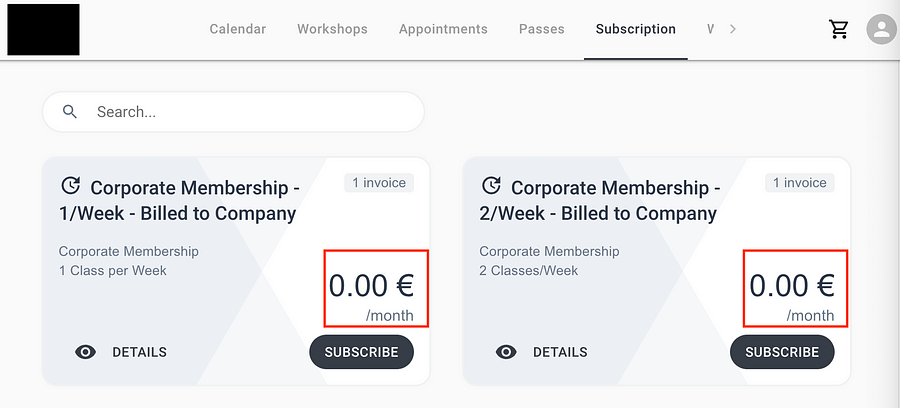
You can access that page and “buy” a free subscription by changing the value of a parameter in the [GET] request. Originally, the value was set to false.

What happened here is that the client (me) has specified in its URL request being sent to the server (the backend of the software) that they are asking to view the managers only page, as I modified its value to true. Since there was no server-side verification, they assumed that my regular account was allowed to access that page.
Once you arrive on the manager’s page, you are then asked to make a purchase of 0.00€ for a corporate pass subscription. I used a popular neobank to make a purchase using a temporary credit card. Here is the proof of “buying” a free corporate pass for 0.00€ 🙂
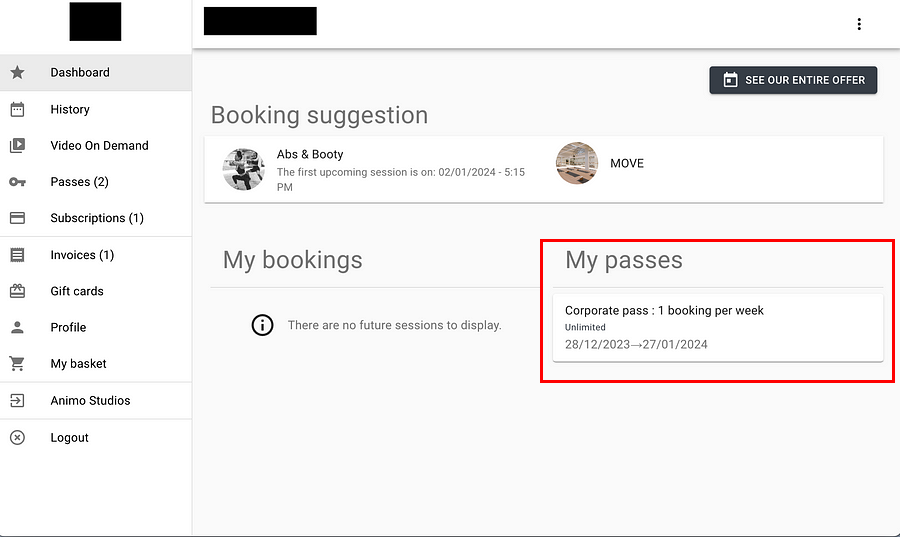
Once I discovered the vulnerabilities, I contacted the SaaS provider to notify the issues. They were very quick to respond, and their software development team have patched the vulnerabilities very quickly. They were very grateful for my findings and have made communication a pleasure. This kind of appreciative behavior is greatly valued.
I also notified the sports club I usually go to and they were very kind and offered me 5 free classes.
Thanks for reading the blog post!

Leave a comment